How to Scan a Document: A Comprehensive Guide Introduction In the modern digital world, the ability to scan documents efficiently and accurately is crucial for individuals and organizations alike. Whether you need to digitize paperwork, preserve important records, or share information electronically, a scanner can be an invaluable tool. This comprehensive guide will lead you …
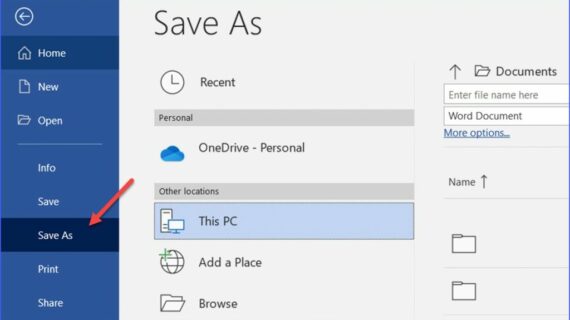
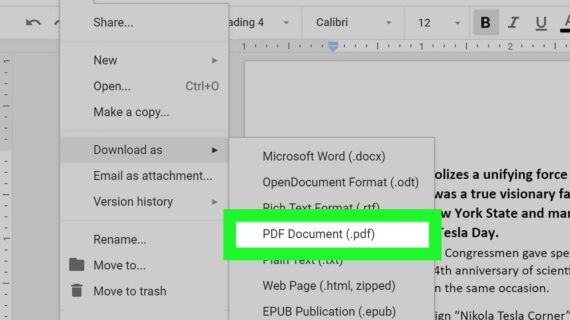
How Do I Save a Word Document as a PDF?
How to Save a Word Document as a PDF Benefits of Saving a Word Document as a PDF Saving a Word document as a PDF offers several advantages: Portability: PDF files are compatible across multiple platforms and devices, ensuring easy sharing and viewing. Universal Accessibility: PDFs can be accessed by anyone with a PDF reader, …
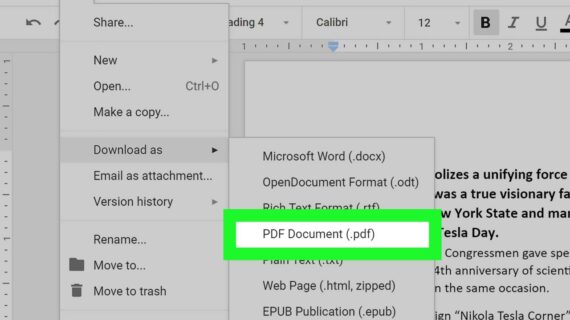
How Can I Turn a PDF into a Word Document?
How Can I Turn a PDF into a Word Document? Portable Document Format (PDF) files are a ubiquitous file format that is used for sharing documents across different platforms and devices. However, PDF files are not as easily editable as Word documents, which can be a problem if you need to make changes to the …
How Can I Digitally Sign a PDF Document?
Definition of Digital Signature A digital signature is an electronic signature that verifies the authenticity of a digital message or document. It is similar to a handwritten signature, but it is created using a cryptographic algorithm. Digital signatures are used to ensure that the sender of a message is who they say they are and …
Document Translation Services in the US?
Document Translation Services in the United States: An In-depth Analysis Introduction In today’s globalized world, businesses and individuals are increasingly required to communicate across language barriers. Document translation services play a crucial role in facilitating this communication by enabling the translation of documents from one language to another. The US, being a hub for international …
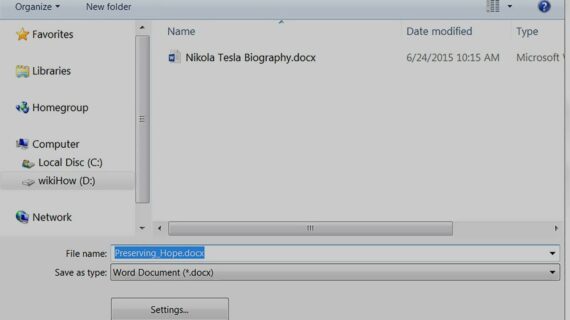
How Do I Change a PDF to a Word Document?
How to Convert a PDF to a Word Document PDF (Portable Document Format) and Word documents are two of the most widely used file formats in the world. PDFs are great for sharing documents that need to maintain their formatting, such as official documents, presentations, and reports. Word documents, on the other hand, are more …
How to Put Signature on PDF Document?
How to Put Signature on PDF Document? A PDF (Portable Document Format) file is a versatile and portable file format that can be viewed and printed on various devices. It is often used for sharing documents that need to maintain their original formatting and layout. One of the essential features of a PDF document is …
How to Switch PDF to Word Document?
How to Switch PDF to Word Document: A Step-by-Step Guide for 2023 In the digital age, documents in Portable Document Format (PDF) have become ubiquitous. Their versatility and ability to preserve formatting have made them the go-to choice for sharing information across different platforms and devices. However, there are times when you may need to …
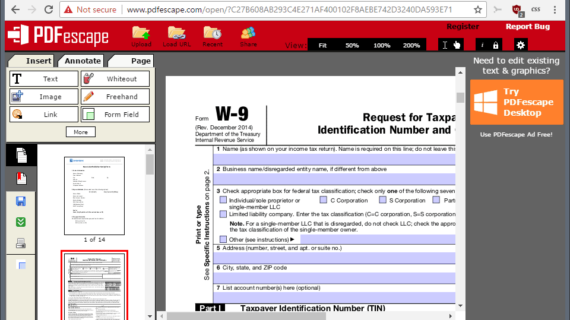
How to Edit PDF Document for Free?
How to Edit PDF Documents for Free: A Comprehensive Guide Introduction PDF (Portable Document Format) files are a widely used format for sharing documents that preserve the original formatting and layout. However, there may be instances when you need to edit or modify the content or appearance of a PDF. This is where PDF editing …
How Can I Type on a PDF Document?
How Can I Type on a PDF Document? Overview PDF documents are a common file format used for sharing documents across different platforms and devices. They are often used for official documents, presentations, and other important documents that need to be preserved in their original format. However, PDF documents are not natively editable, which means …